Originated by the ‘Wizard Spider’ Russian hacking group, CONTI ransomware is an evolution of one of the group’s most successful ransomware – Ryuk. CONTI is a more accessible version of Ryuk, built for distribution by affiliates in a ‘Ransomware as a service’ model. CONTI ransomware was first spotted by cybersecurity teams in May 2020 and claim to have over 150 successful extortion attacks by the end of 2020, with at least $20M in revenues paid by the victims.
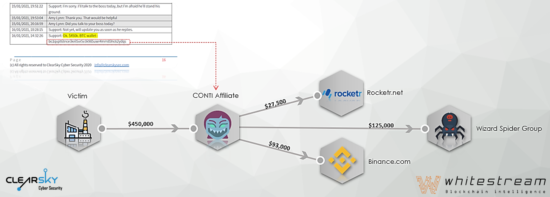
During our routine monitoring of ransomware groups, we detected a sample of the CONTI ransomware uploaded to Virus Total from Canada. We were able to access the entire negotiation process between the company and the extortion group in real time by analyzing the sample. Furthermore, we succeeded in following the ransom payment, tracking all of the involved bitcoin blockchain transactions. In this report, ClearSky and Whitestream, we uncover the negotiation process between this adversary to the extorted company, following by the Bitcoin Tracking.
Read the full report: CONTI Ransomware – Negotiation and Bitcoin Tracking
The revealed bitcoin transactions allowed us to associate CONTI with Wizard Spider, as Ryuk was previously associated with the group. This association confirms the common theory that CONTI and Ryuk are connected. Following the negotiations closely assists in learning how to properly engage with the attackers, managing the most sensitive part of a ransomware attack.
Acknowledgments
We would like to thank the security researchers from Whitestream.io that worked on this report with us, and Moty Cristal who shared information and provided feedback, which have been crucial for this research.