Empower your cyber defense shield with Actionable threat Intelligence
ClearSky is comprised of Intelligence researchers and cyber experts, who monitor, analyze and categorize attack groups and cyberattacks around the globe. Our experts monitor and assess methods, infrastructure, tools and targets of APT groups and other cyber attackers, 24X7.
We use our own set of unique tools going “deep down” into their gathering places and evaluate their cyber weapons and their attack infrastructure. We serve organizations by going far beyond the company’s perimeters, collecting relevant and customer-specific data, giving them early warning alerts and actively helping them mitigate attacks.

Our unique ClearSkySec© methodology is based on years of experience in mitigating cyberattacks for the financial sector, the public sector, as well as expertise in Pharma and critical infrastructure sectors.
We know that every organization has its own unique set of cyber threats, state related, sector related, application related, as well as different preventive methods deployed to mitigate attacks. We know that SIEM and SOC personnel cannot cover all aspects of cyber defense, and we assist them on a daily basis to confront new threats.
Our Threat Intelligence solution provides an external protection layer added to current existing internal layers. Using our ClearSkySec© methodology we provide critical data to help organizations to focus their security resources on relevant cyber threat prevention.
Solution components
- Threat map and enhanced vision of cyberspace
- Mapping main attack groups targeting the organization
- List of weapons and infrastructures possessed by the attackers
- Attack vectors that are being deployed by each actor
- Identifying vigilant and activist hackers
- Real-time cyberattack operations team
Packages
ClearSky offers sets of service packages for our customers:
- Bronze Plan – Executive briefing (C3/CISO)
- Silver Plan – Sector specific alerts + Executive briefing
- Gold Plan – Customer specific alerts + Sector specific alerts + Executive briefing
- Platinum Plan – Active Response + Customer specific alerts + Sector specific alerts + Ex. briefing
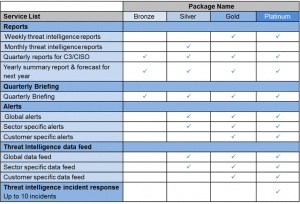
Threat Intelligence Service description:
Reports:
Weekly threat intelligence reports
- Customer specific cyber alerts
- Sector specific cyber events/alerts
- Weekly updates regarding our investigations of APT groups and other malicious actors.
- Review and analysis of critical cyber events.
- Technical indicators (IOC’S – Indicators of Compromise) in CSV file – to monitor, investigate and block past and current threats.
Quarterly high-level reports for Executives
- Overview of major cyber events in the last Quarter including:
- Major APT events
- Major attack vectors
- New attack patterns and risk assessment
- Significant leaks of data
- Our Insights from the past quarter events
- In-depth analysis of notable events
Yearly report & next year forecast
Overarching review and analysis of:
- Most significant attackers and actors – activity, methodology, tools and objectives. Further, we provide insights regarding the global factors (such as political, technological and economic) affecting cyber space.
- Most significant types of attacks – break-down of the most common and/or damaging attack vectors and tools.
- Most notable events and trends – break-down of the most significant events and trends that took place throughout the last year.
- Forecast – our assessment for the coming year regarding all the above mentioned factors and points.
- Timeline – an overarching and comprehensive timeline spanning the entire past year, including:
- Targeted entity
- Affected countries
- Affected sector/industry
- Short description of the event + insights
Threat Intelligence Alerts
- Global alerts – investigation findings and analysis of major events affecting multiple sectors and/or regions.
- Sector specific alerts – investigation findings and analysis of critical events affecting specific sector, industry and/or region.
- Customer specific alerts
- Analysis of findings from our ongoing monitoring of suspicious activity pertaining the client:
- Monitoring of major social media platforms
- Strategic analysis of cyber incidents.
- Intel gathering of any malicious actor targeting the client.
- Investigation findings and analysis of critical events pertaining specifically to the client
- Analysis of findings from our ongoing monitoring of suspicious activity pertaining the client:
Threat Intelligence data feed
Near real-time IOC Feed system (Global or Specific) – interfaces with your organization's security monitoring
systems. The feed can be easily adapted to your organization's needs and demands. This feed is based on data and
intelligence research regarding global threats, sector specific threats, or customer specific threats.
Threat intelligence incident response (Up to 10 incident a year)
On-call assistance in investigation and mitigation of cyber incidents, including but not limited to:
- Generic phishing attacks.
- Targeted phishing attacks, including BEC (Businesses Email Compromise) attacks.
- IT and database breaches, including assessment of data compromise and/or exfiltration.
- DDoS attacks
- Malicious website attack or other digital infrastructure attacks. E.g. defaced websites, C2 servers, waterhole
phishing websites impersonating the client of targeting its employees and/or customers. - Malware attacks, including ransomware and spyware.
- Extortion attempts, including malware-extortion, data-leak extortion, etc.